Protection against data theft and industrial espionage!
The web browser knows no boundaries—and that is precisely what makes it dangerous. It accesses the internet and internal data at the same time—a perfect target for cybercriminals. Where convenience and risk meet, IT’s greatest vulnerability begins.
Traditional security fails
The Web Browser: A Doorway for Attacks
In many organizations, the web browser runs directly on the workstation PC within the internal network. This means that web content from the internet is processed directly in the internal environment – a risky principle.
This is because a locally installed browser is a central gateway: it has simultaneous access to the open Internet and to sensitive internal data (see diagram). This dual function makes it particularly dangerous. If attackers can exploit security vulnerabilities in a browser, it is almost impossible to prevent the leakage of confidential information.
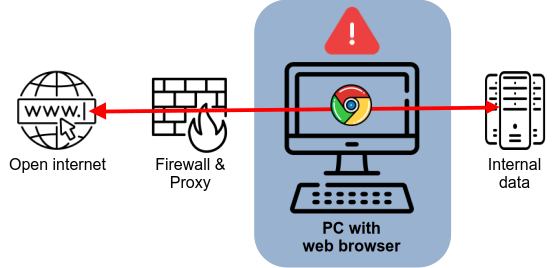
It also does not matter whether the browser runs directly on a PC, is operated in a terminal server environment, or is executed locally in a virtualized environment. In all cases, there is no separation between the internal IT environment and the Internet, because the actual problem lies in the browser itself: it is a complex software package with many potential security vulnerabilities.
Vulnerabilities in web browsers 2024
Although it would be technically possible to completely separate the internal network from the internet (“dual network”), this would be virtually impossible to implement in everyday working life. Internet research, web applications, and multimedia content are simply part and parcel of modern-day production, administration, and communication.
Even reactive defense systems such as intrusion detection systems (IDS) or virus scanners only help to a limited extent. They only recognize known attack patterns – while new malware and attack techniques emerge every day. The race between attackers and defenders thus remains a hopeless game of cat and mouse. Classic security mechanisms inevitably reach their limits here.
And traditional “protective measures” such as URL filters, content blocking, or blacklists offer no protection. They only create an illusion of security, cause additional effort, and completely ignore the actual cause of the problem.
The solution
The Two-Browser Strategy
The ideal web browser provides unrestricted Internet access without compromising internal data or systems. This results in one key requirement: the browser must not be run on the internal network, but must remain secure and convenient to use from the workplace. These seemingly contradictory goals are achieved securely and efficiently by a remote-controlled browser system (ReCoBS) as part of a two-browser strategy.
With a ReCoBS, the web browser is not operated on the internal network, but on a dedicated ReCoBS server within the DMZ (see Figure 2). All web content is processed there and then transmitted to the workstation exclusively as encrypted image and sound data. The user controls the browser conveniently via mouse and keyboard – just as usual, but much more securely.
The decisive security advantage:
The internal network can now be completely isolated from the open internet by means of appropriate firewall rules. This makes it essentially inaccessible to attackers, while reliably preventing unwanted data leakage. The result is effective and practical protection against attacks on the internal network via the web browser – without any restrictions in terms of functionality or convenience.
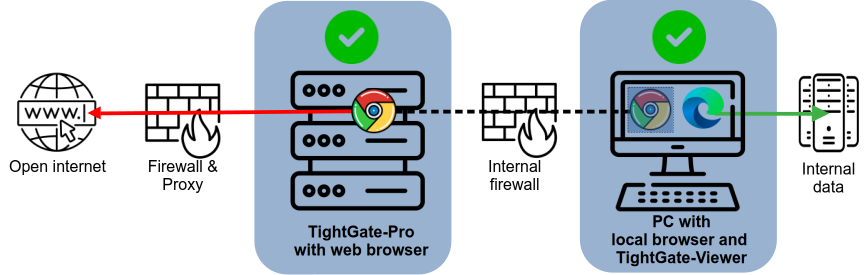
TightGate-Pro
A user-friendly two-browser solution
TightGate-Pro consistently implements the two-browser strategy:
The Internet can be used securely via the browser in TightGate-Pro, and the local browser remains available as usual for internal applications and specialized procedures (Figure 3).
For users, hardly anything changes: they surf, search, and use web applications as usual—only much more securely. The display of the TightGate-Pro browser is transmitted to the workstation in real time as a graphics stream; it is conveniently controlled via mouse and keyboard from the local computer.
The MagicURL link switch, which is part of TightGate-Pro, ensures that you don’t have to switch between browsers. It ensures that clicked links are always opened in the correct browser. This keeps usage intuitive, high-performance, and familiar, while TightGate-Pro secures all Internet traffic in the background.
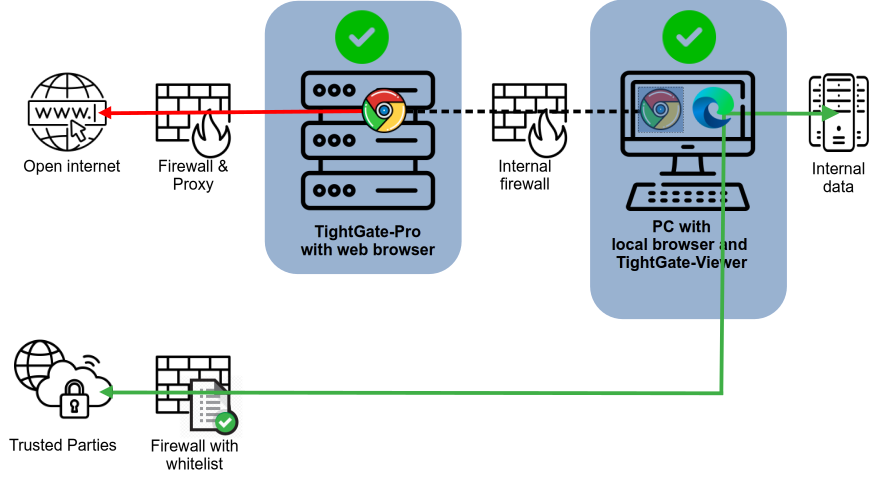
Real Security, Not Just the Illusion of Protection
TightGate-Pro consistently separates where others only shield:
The browser for the Internet runs outside the internal network and has no access to internal data. This prevents malicious code from being introduced from the Internet and eliminates the risk of unauthorized access.
The internal browser, on the other hand, remains available for internal applications and trusted remote stations. Since it now has no Internet access, it can no longer be misused to download malware or leak data.
Even accidentally opening email attachments, visiting dangerous websites, or following questionable links no longer gives an attacker from the Internet access to internal data.
A key component of IT security
TightGate-Pro is the central component of an effective security concept for securing Internet access.
Only with TightGate-Pro can an effective ReCoBS protection concept based on a two-browser strategy be reliably implemented.
While other approaches fail because either there is no effective separation of the web browser from internal data or the connection to the separate browser itself offers new areas of attack, TightGate-Pro impresses with complete separation, secure transmission, and unrestricted functionality.
Its strength lies not only in security, but also in its high level of user comfort.
After all, security only works if it is accepted: a system that requires workarounds or makeshift solutions is doomed to failure in the long run. TightGate-Pro, on the other hand, offers protection that integrates seamlessly into everyday work.
The hardened architecture is designed for continuous operation and high reliability.
Even under heavy load or increased attack pressure from the Internet, access to web content remains stable, high-performing, and guaranteed at all times.
Certification
Security that stays secure
TightGate-Pro (CC) 1.4 is designed for highly sensitive environments and was certified by the BSI (BSI-DSZ-CC-0589) in 2015 according to Common Criteria EAL 3+. The formal certification expired in 2020 as scheduled; the underlying protection mechanisms remain effective unchanged.
Comparing secure browsing
Explained in detail
Why there is no such thing as a 100% secure browser, which risks really matter and which options the BSI recommends. Everything at a glance – from the BSI minimum standard for web browsers to the optimum solution of a separate browsing environment.
The top 5 for ‘safe surfing’
The big picture
1) Locally secured web browser
2) Microvirtualisation
3) System virtualisation
4) Surfing via terminal server
5) Separate browser via ReCoBS
